AWS Organizations 2: Role Switching
Account switching can get troublesome. Luckily, AWS Organizations lets you streamline this process.

This is the sequel to AWS Organizations 1: Getting Started
So I recommend reading the above first before moving forward.
This article highlights the convenience of being an admin at a management account.
Under normal circumstances, each account would have an IAM user with admin powers, aka the admin user.
Having, so many accounts mean managing credentials for each one. A problem that becomes more annoying with more accounts.
Luckily, as the admin of the management account, there's a way for you to assert your dominance in the other accounts without login in as their respective admins.
You would simply create a role with admin powers, then when you switch accounts, you assume that role giving you admin rights to the respective account (I swear this will make sense later).
If this peaks your interest, then you're in the right place.
But first, some theory!
What it means to "Assume a Role"?
I'm going to try and explain this using an analogy so bare with.
Imagine each of the AWS account in our organisation as a separate building. You have the HQ (management), then you have two other locations (Dev and Prod).
Assuming a role is like going to visit one of the other buildings - lets say Prod.
Upon arrival, you walk into the lobby and show the receptionist your credentials proving that you are an administrator from HQ - they have checked their list of allowed personnel and determined that you are a trusted entity.
The receptionist then gives you a key card with full access to the entire building. Any room you want to go into, just scan that key card and you're in.
The key card lets you walk around with admin powers in the Prod building - it lets you, someone who doesn't work in the prod building, assume the role of an administrator of the prod location.
You can go anywhere and do anything. No limited "visitor passes" for you because you're important!
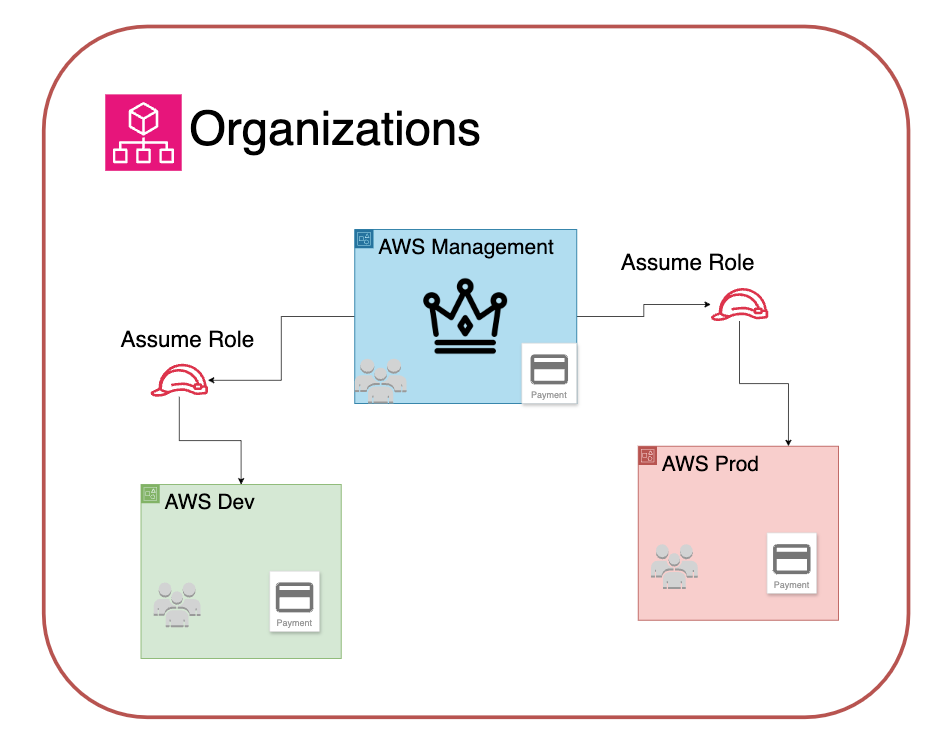
AWS lets you do something similar (after some initial setup).
In either the Dev or Prod accounts, you can create a role for the management account.
Then, from the management account, you can assume that role (collect your key card) when you switch to either Dev or Prod.
If you read all that and understood it the first time, then congratulations, you are much smarter than I am (or I'm just that good at explaining).
If it didn't make sense, read the rest of this article and follow along using your own organisation, then read the above again. Hopefully, it will make sense the second time around.
Now that we have the theory out the way, time to get our hands dirty.
Creating a Role
Log into any one of your non-management accounts (as admin) and navigate to the IAM console then click on Roles (on the left), the select Create role
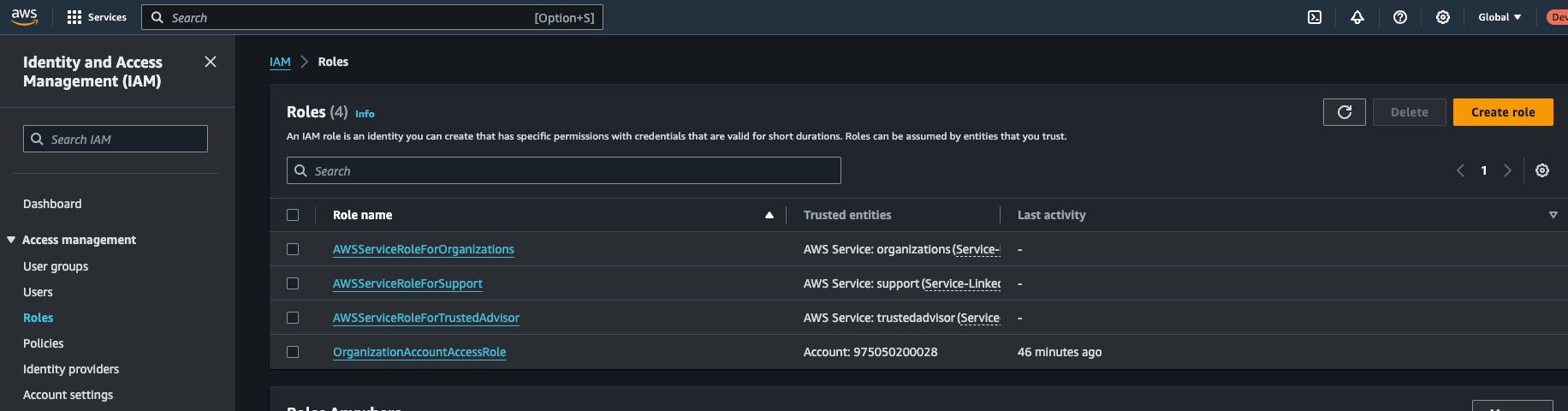
Here you will specify a trusted entity.
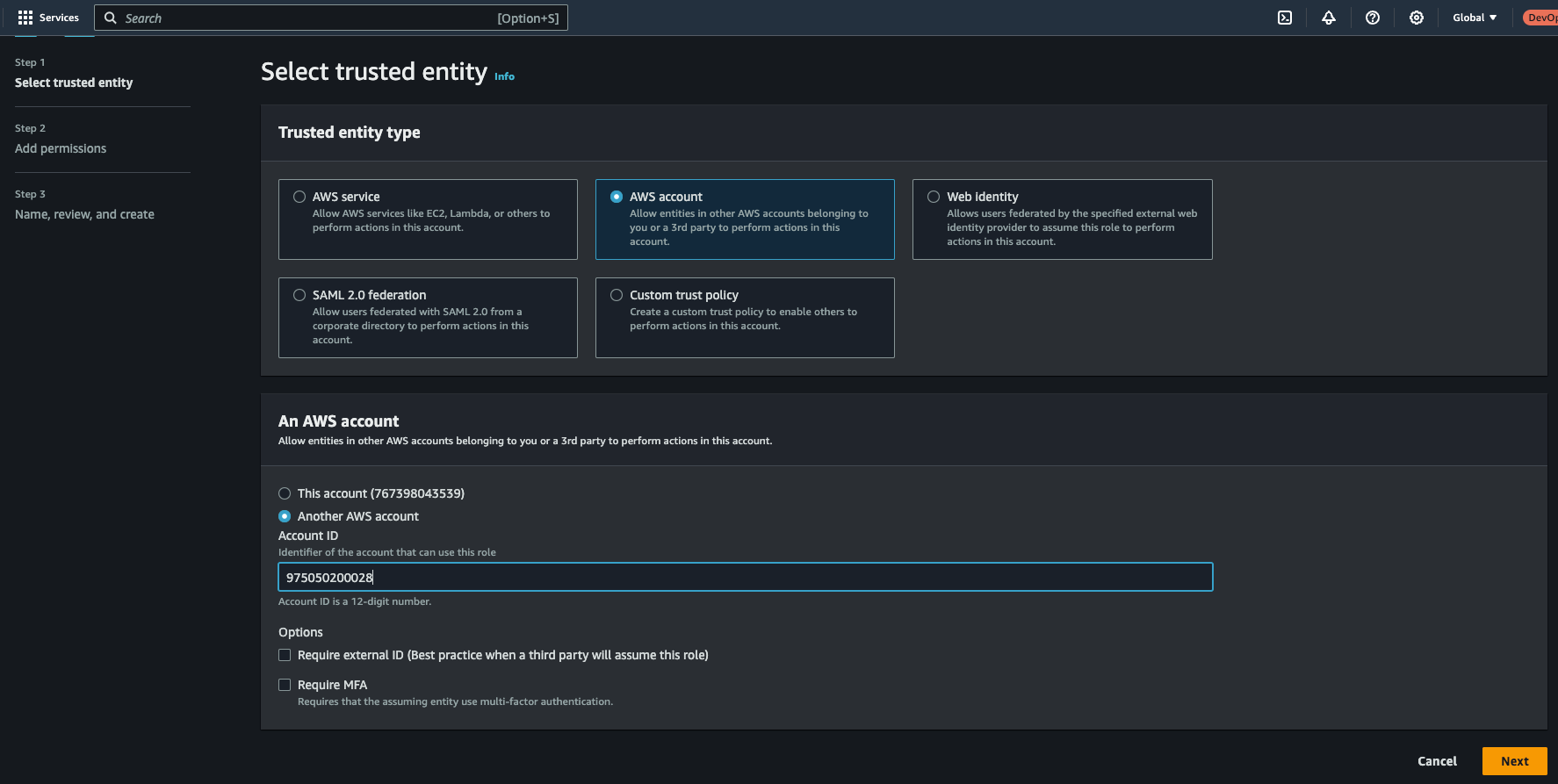
Choose AWS account then select Another AWS account option.
Input the account ID for the management account and click Next
Time to assign permissions to the role. You will want to give the management account admin rights so be sure to select AdministratorAccess
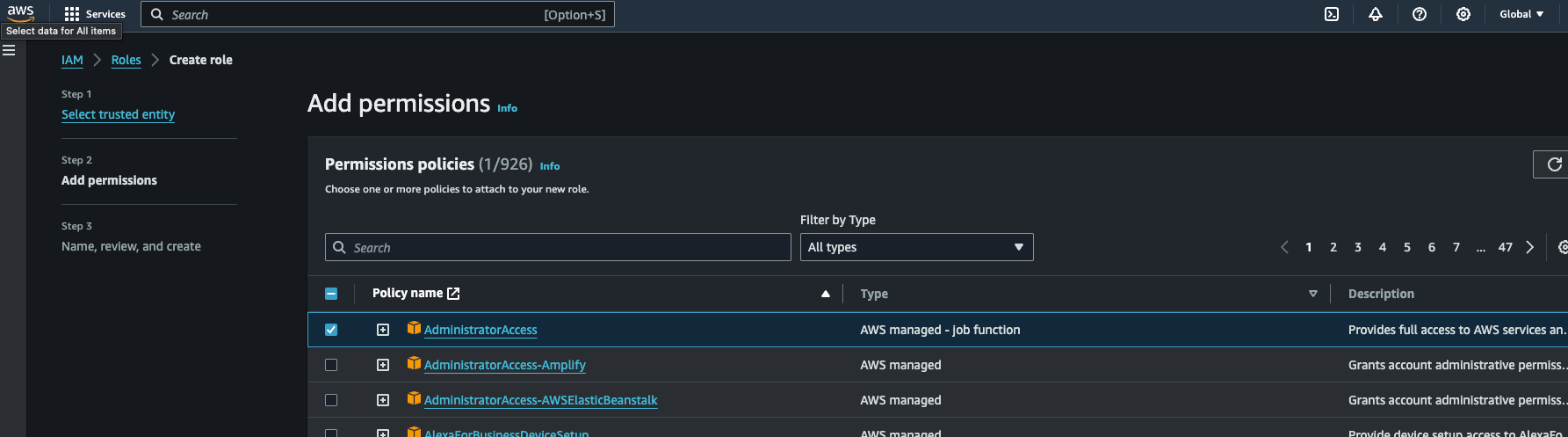
Scroll down and click Next
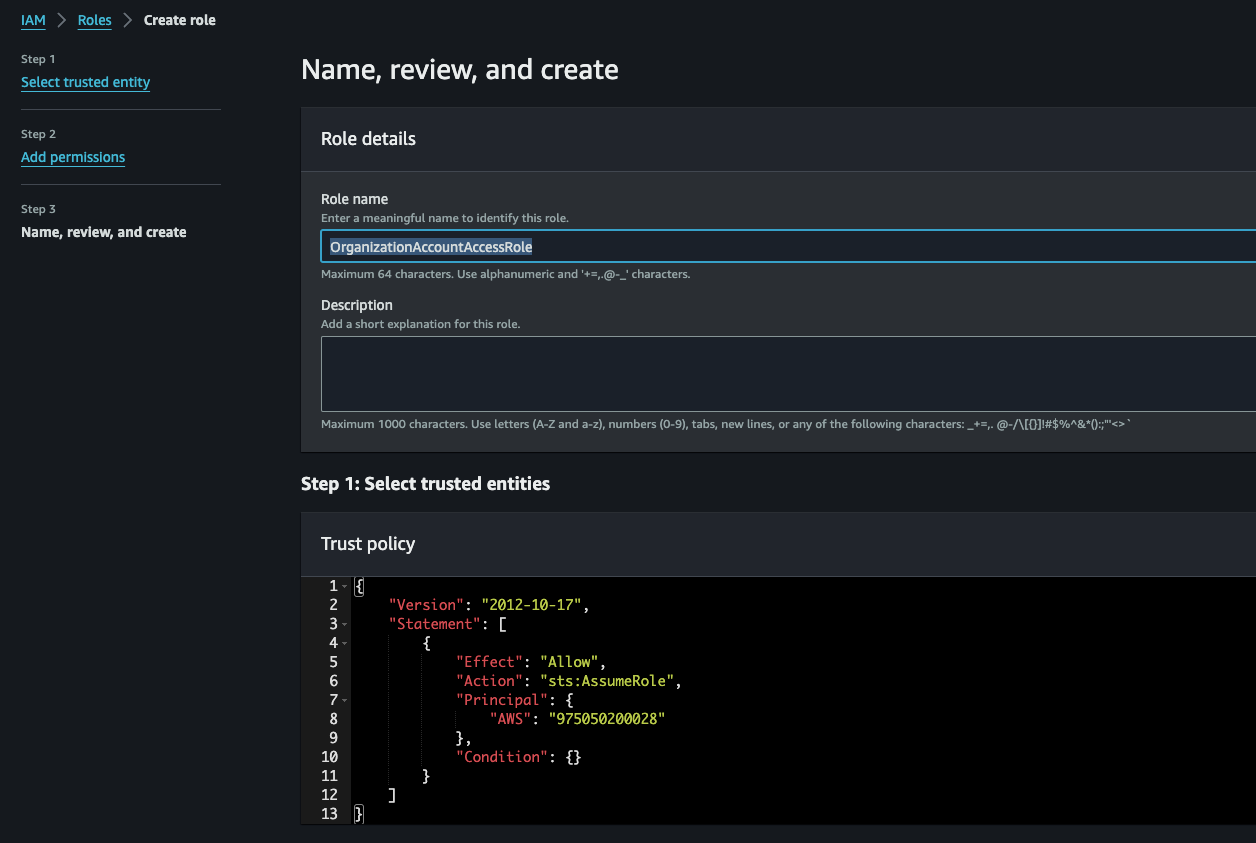
Name the role OrganizationAccountAccessRole
Scroll down and click Create role
You can call the role whatever you want but there is a reason why you should name it OrganizationAccountAccessRole
It is important to note that there are two way to add an account to your organisation.
- Option 1: Add an existing account (shown in the previous article), the second is to create it from AWS Organisation.
- Option 2: Create the account from AWS Organizations
If you opt for option 2 then the role creation will be taken care of for you and it will be named OrganizationAccountAccessRole
Great, we now have the role!
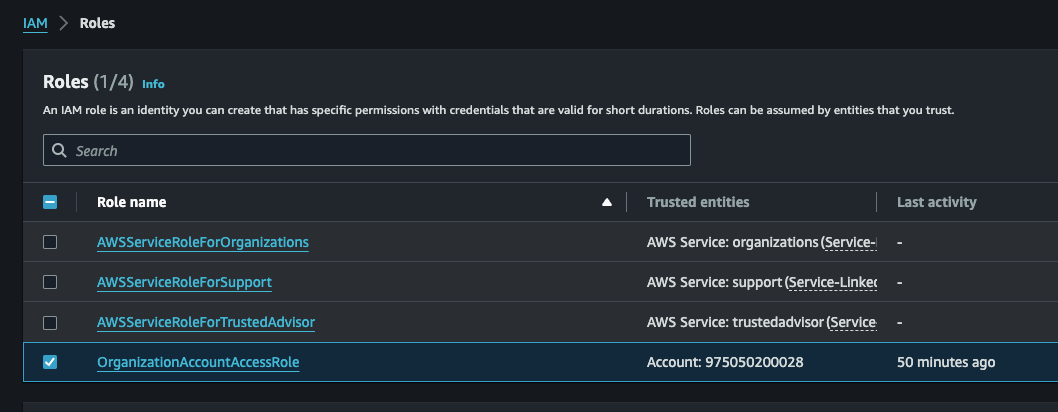
Click on the newly create role and then navigate to Trust relationship
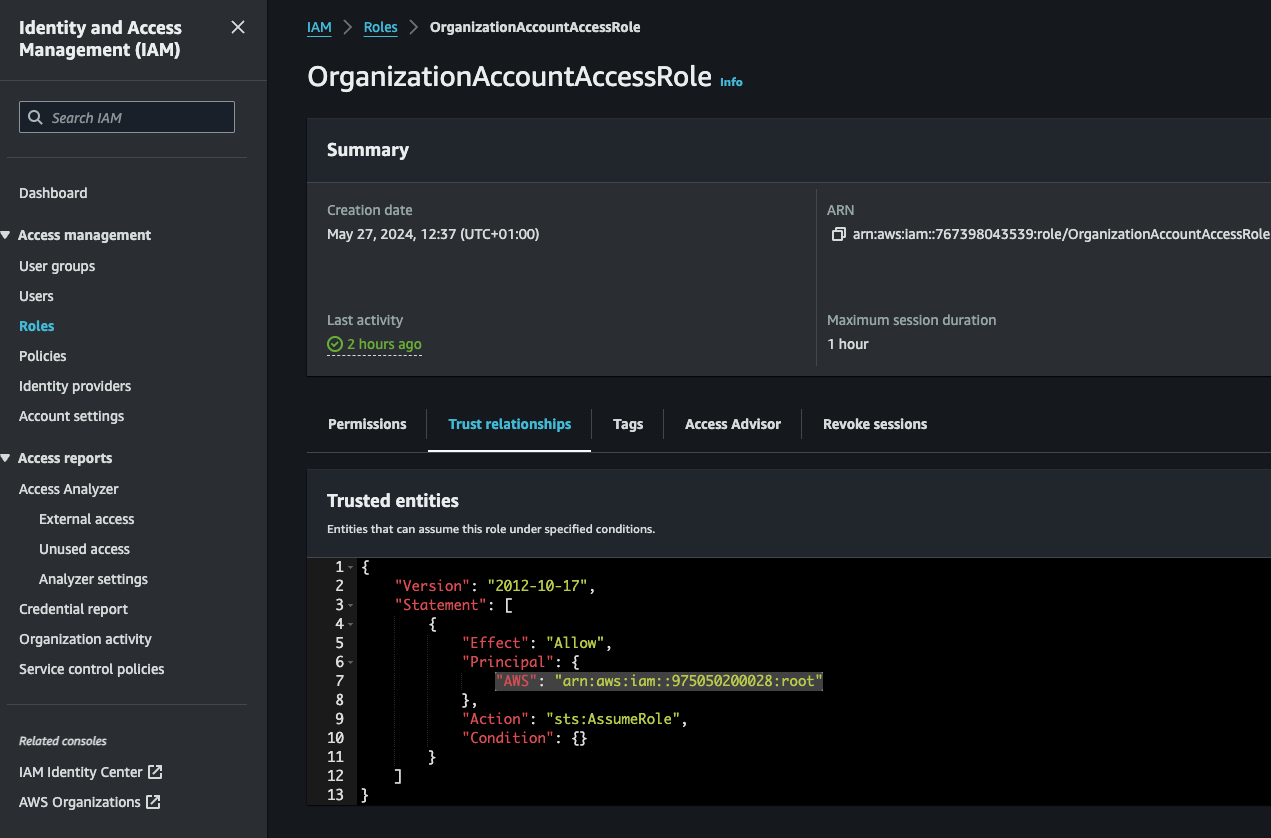
Here, you can see a JSON of all the trusted entities - so far it's just the management account.
Remember from my analogy, where the receptionist checks their list of allowed personnel?
The trust relationships JSON is that list. It tells AWS who is allowed to assume that role and get the admin key card.
Now that the role is created, it's time we used it.
Switching Accounts from Management
Go back to the management account and click on the profile dropdown on the top right.
Click the Switch role button.
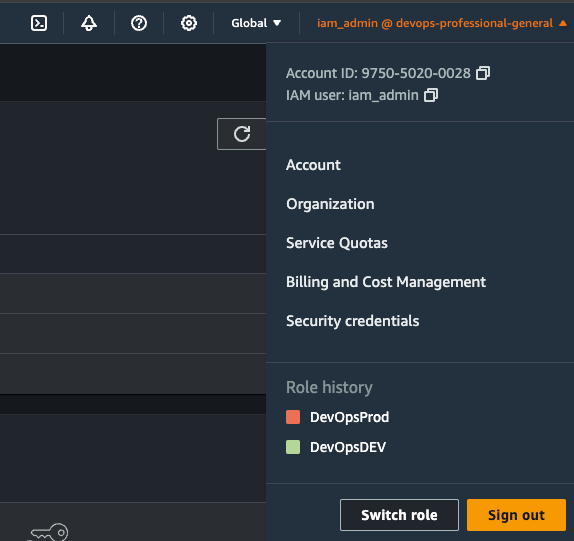
You'll be greeted with a form. Make sure to fill these out with the account ID of the PROD account.
For IAM role name, copy and paste the name of the role you just create: OrganizationAccountAccessRole
Be sure to give a display name, this will make it easier to recognise later.
If you want to colour code the account name then go for it. Personally, I like this setup:
- Dev: Green
- Staging: Amber/Yellow
- Prod: Red
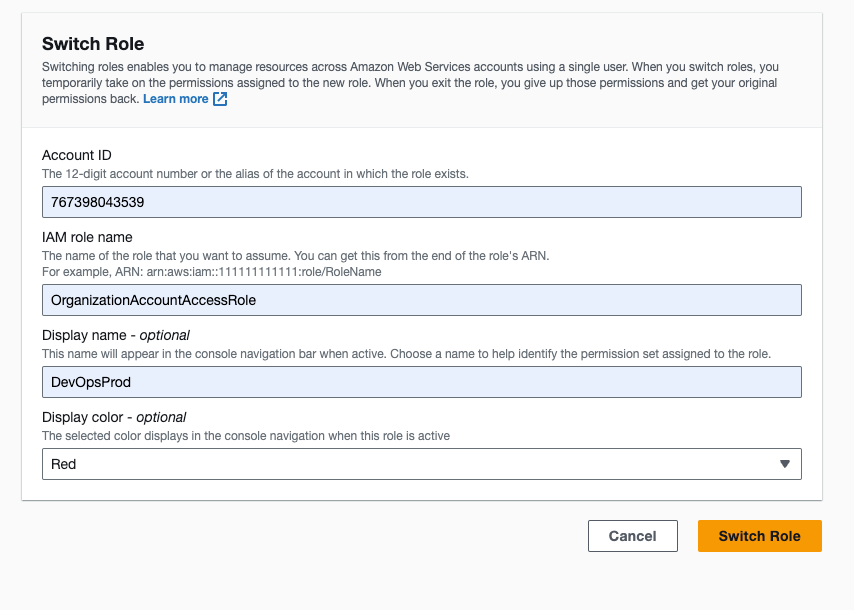
Once your done, click Switch Role and you will be sent to the dashboard of the account you just added - in my case, the prod account.
You'll know if it worked if you can see the profile name on the top right changed to the display name and colour you specified.
For me it's "DevOpsProd" with a red background.
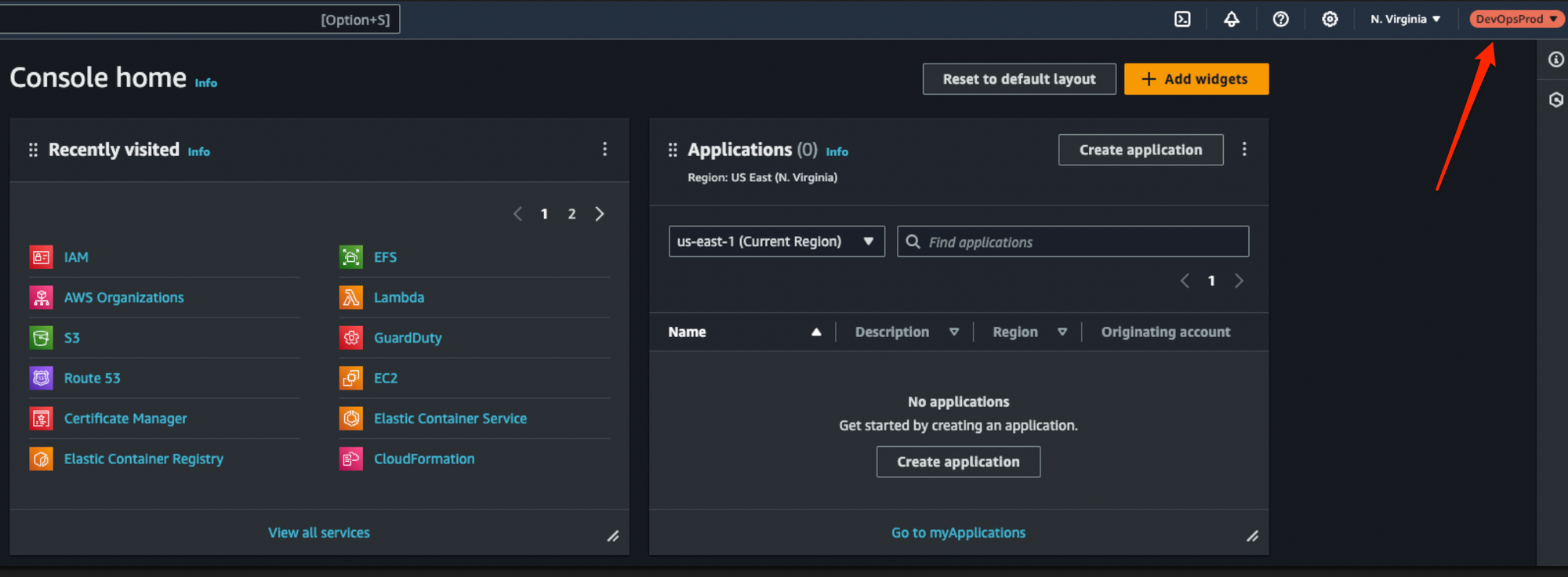
If you want to switch back to the general account, click on the profile and click Switch back
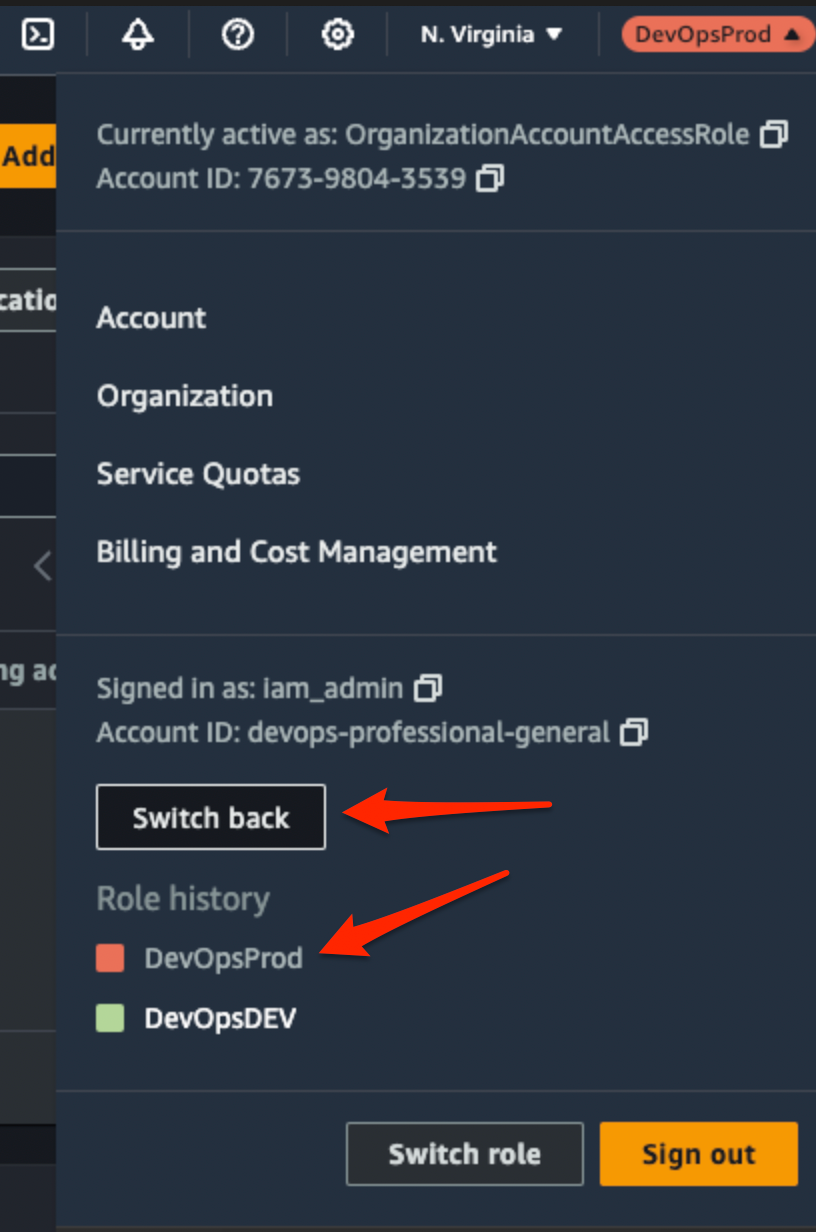
You can now switch between accounts at the click of a button!
Simply select the display name (I've already added Dev) under role history and your back in! Easy!
You don't even have to go back to the management account, you're now able to switch between accounts on the fly.
Hopefully, you can now see how much easier life of an admin can be when you know these simple tricks.
